Below you will find one simple solution for crackme found in ".Net" category: CrackMe By Rayko.
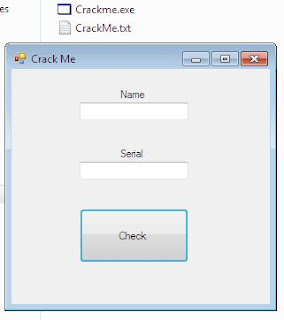
Unzip the file and run it. You should see screen similar to the one below:
As you can see, there are 2 fields, Name and Serial. But... we will not search for any serial here.
I found a different solution. Check it out:
Normal behaviour of the program looks like this:
So if name and/or serial is not valid, program will show us 'Try again' message (so called 'badboy').
Let's findout what's going on.
To check how this program works, we will use .Net Reflector (but you can use any other tool designed to do the same, for example ILSpy). In my opinion "right now" it's a good moment to make a copy of the target program, let's name it 'crackme-copy.exe'. ;)
Let's analyze the app. The most interesting is Form1:
Simple. As I already said before, we don't need to know the real serial. We can change the flow of the application to bypass verification. To do that (and to check how it can be done) let's switch the view to IL mode. Now we can see a ".NET ASM" ;) Let's analyze it line by line to check where "if-else" occurs:
As you can see, we are in a good place to start. Case for now is to check what each line means.
To do that, we can use this or this list. (By the way, it's always good to check at Google, maybe you can find some hints directly from the vendor, for example: here.)
So what we need to do is to understand which line should be changed (to what) to change the flow of the application. Now we will check those lines:
Before that - a little translation:
Yes, it is NOP instruction, so application will move directly to the next one, ldstr to print (the 'badboy') message "Try Again".
Now, if we will change the brfalse to brtrue we should be able to bypass restriction and get the ('goodboy') message. To do that, we need to open our crackme in HxD (or similar program).
Now we need to go back to our table with IL commands and opcodes to "generate" a list of opcodes to look for when we're watching the file in HxD. What we need to change now is brfalse (code: 0x2c) to brtrue (with code: 0x2d). Change all instructions to opcodes and find the (hex) line in HxD. Now You will know where 2c needs to be changed to 2d. ;)
(Small hint: use copy of the crackme to compare it with original file (Ctrl+K in HxD).)
After changing the copy-file, we can see that there is a one small change in the crackme-copy.exe:
Game over. Now?
Let's do another one... ;)









No comments:
Post a Comment
What do You think...?